1. Introduction
Correctional facilities are always struggling with overcrowding and understaffing, creating dangerous and stressful working conditions for correctional officers. It is crucial to ensure that prisons are equipped with the latest technology to provide maximum security and maintain order. The electronic key management system is an innovation that has proven to be a game changer. This blog will delve into the need for key control systems in prisons, explore their features and benefits, and highlight the importance of key management for the safety of prison inmates.

Correctional facilities are locked facilities. Cellblock doors, security gates, staff area doors, exit doors, and food slots on cellblock doors all require keys. While some large doors may be opened electronically from a control center, the backup system in case of power failure is a key. In some facilities, the use of keys includes the old fashioned metal kind and the newer computer locks where a computer card is swiped across a pad that opens a door. Keys also include handcuff keys and keys to restraints, which could be a prized possession for an inmate if stolen or lost by a correctional officer. Key control is basically common sense and accountability.
Correctional officers should not allow prisoners to knowingly or unknowingly gain access to prison, work center, courthouse, or vehicle security keys. Allowing a prisoner to use any security key, whether intentional or negligent, could be grounds for disciplinary action, up to and including dismissal. Besides post or housing keys used by the officer inside the facility, there are emergency keys and restricted keys.
Guards have a poor understanding of their role, severely inhibiting their ability to control and care for detainees. In most prisons, for example, many guards had delegated to varying degrees much of their power and functions to detainees. Core functions, such as key control, were observed as mainly in the hands of nominated detainees.
How do you manage keys when one or more key control officers are out? Remember, the same COs who might not perform a routine inmate check as scheduled, are being asked to fill out a manual access log for keys. Remember, the same COs who might already falsify other records, such as routine inmate checks, are being asked to fill out a manual access log for keys. Are you confident they’re completing the key log accurately?
Poor key control, raising concerns for inmate safety.

2. Why Key Control is Needed?
Security is an important issue in prisons due to the presence of dangerous prisoners and the high likelihood of violations and escapes. Traditional methods of physical key control rely on manual logs and paper-based systems, which are prone to human error and unauthorized access. This requires a more efficient and secure system for managing prison keys. The implementation of an electronic key management system provides correctional facility staff with an automated and advanced method of key handling, ensuring complete control and accountability.
3. Features and advantages of the electronic key control system
Electronic key management systems offer a variety of features that can significantly enhance prison security. These systems are equipped with biometric authentication, ensuring that only authorized personnel have access to the keys. In addition, they provide comprehensive tracking and logging, recording details of every key movement from launch to return. Real-time alerts and notifications are also incorporated, enabling immediate response to any suspicious activity, such as unauthorized key access or attempted system tampering.

3.1 Key security
Keys are stored in a sturdy solid steel key cabinet to prevent tampering and theft, even if other layers of security have failed. Such systems should also be kept in a central location so that prison officers can quickly access the keys.
3.2 Key index and number
Utilize RFID key fobs to index and electronically encode each key so keys are always organized.
3.3 User roles with different access levels
Permission roles grant users with role management privileges administrative privileges to system modules and access to restricted modules. Therefore, it is completely necessary to customize the role types that are more applicable to the corrections.
3.4 Restrict access to keys
Access control is one of the most fundamental claims of key management, and access to unauthorized keys is an important area that is regulated. “Who can access which keys, and when” should be configurable. The administrator has the flexibility to authorize users for individual, specific keys, and it can completely control “who has access to which keys”. The key curfew function can effectively limit the time of key access. The physical key must be used and returned at the scheduled time. When the time is exceeded, an alarm message will be generated immediately.
3.5 Event, reason or explanation
When using a security key, the user is required to provide content including pre-defined notes and manual edits and an explanation of the situation before withdrawing the key. According to policy requirements, for unplanned access, users should provide detailed descriptions, including the reason or purpose of the access.
3.6 Advanced identification technologies
A well designed key management system should have more advanced identification technologies such as biometrics/retinal scanning/face recognition, etc. (avoid PIN if possible)
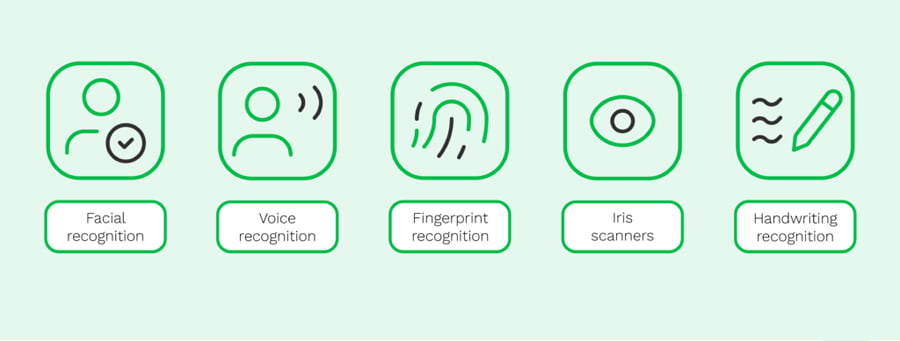
3.7 Multi-factor authentication
Before accessing any key in the system, each individual user should face at least two layers of security. Biometric identification, a PIN or an ID card swipe to identify the user’s credentials are not enough separately.
Multi-factor authentication (MFA) enables businesses to monitor and help protect their most vulnerable information and networks. A good MFA strategy aims to strike a balance between user experience and increased workplace security.
3.8 Key report
The keying system is capable of automatically recording and generating a report of any key indicating the date, time, key number, key name, device location, reason for access, and signature or electronic signature. A key management system should have custom software that enables the user to set up all of these and many other types of reports. A robust reporting system will greatly help businesses track and improve processes, ensure correctional officers are honest and safety risks are minimized.
3.9 Convenience and easy to use

It is useful for authorized users to have quick access to specific keys or key sets. With instant key release, users simply enter their credentials and the system will know if they already have a specific key and the system will unlock for their immediate use. Returning keys is just as quick and easy. This saves time, reduces training and avoids any language barriers.
4. Key management implications for prisoner safety
The benefits of using an electronic key control system go beyond security. They simplify operations and reduce administrative burden by automating key administrative processes. Prison staff can save valuable time previously spent on manual procedures and allocate resources to more critical tasks. Additionally, these systems have the potential to minimize costs associated with lost or stolen keys, ensuring a seamless workflow within correctional facilities.
Effective key management is critical to maintaining the security of prison inmates. By implementing an electronic key management system, prison authorities can ensure that only authorized personnel have access to specific areas, thereby preventing potential harm to prisoners and staff alike. These systems can be programmed to restrict access to certain key holders, thereby limiting the possibility of unauthorized access to cells, medical facilities, or high-security areas. Addressing security breaches in a timely manner by tracking key usage can reduce the risk of violence and escape attempts within prison walls.
In conclusion, the integration of electronic key management systems in correctional facilities is an absolute must in today’s security-driven environment. The advanced features and benefits of these systems increase the overall security of the prison, reduce the administrative burden and most importantly, protect the lives of prisoners. By revolutionizing key control, electronic systems ensure that every key movement is tracked, authorized and meticulously recorded, resulting in a more secure and orderly prison environment. Investments in these cutting-edge technologies underscore a commitment to ensuring the safety and well-being of inmates and staff within correctional institutions.
A good rule for correctional officers to remember is the following: Maintain possession of your keys—at all times.



