What is RFID

What is RFID? RFID (radio frequency identification) is a form of wireless communication that incorporates the use of electromagnetic or electrostatic coupling in the radio frequency portion of the electromagnetic spectrum to uniquely identify an object, animal or person. The principle is contactless data communication between the reader and the tag to achieve the goal […]
Key Control For the Building You Clean
When you own a cleaning company, you need to develop a system for controlling keys. If there is no appropriate system, you may bear an expensive unexpected cost, as lost keys may prompt customers to reset the keys to the entire building. Locks and keys are the most commonly used physical security devices, but they […]
Multi-Users Authentication to Achieve Compliance of Key Control Policy
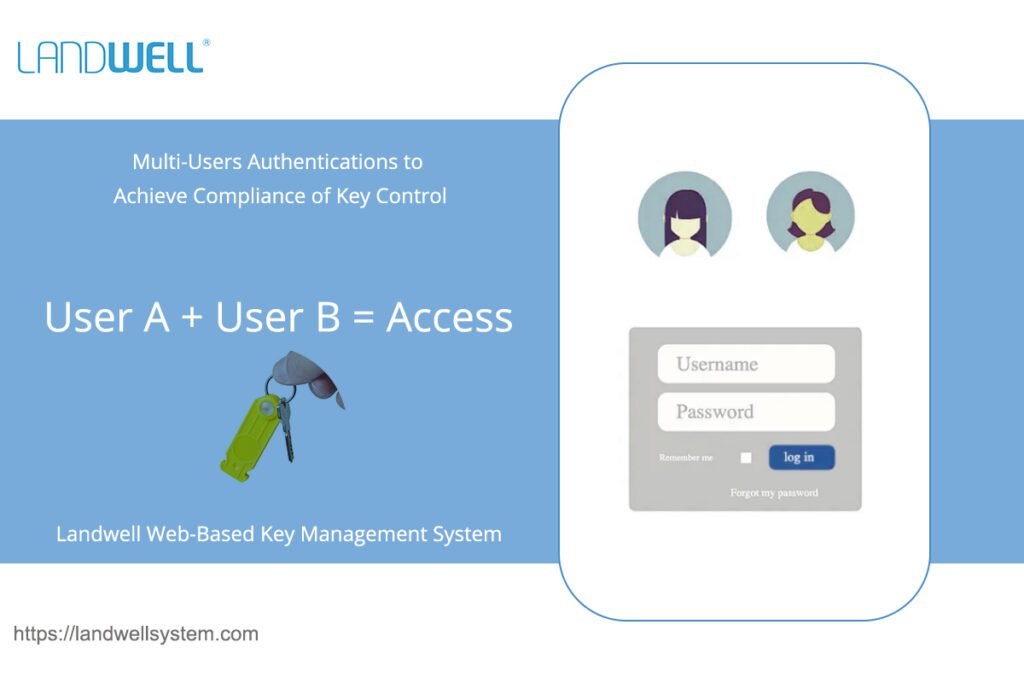
07-03-2024 | by Bruce This article mainly introduces the definition, purpose, and setting method of multiple authentication functions in the Landwell key system, supplemented by examples. Multi-Verification, compliance regulations require login from two or three people, one each from different groups. Similar to the Two-Man Rule, it is a control mechanism designed to achieve a […]
Why do you need key management

Key management can be an important part of an organization’s operations, especially when dealing with large numbers of keys. Here are some ways key management can help operations: Improved security: Key management enhances the security of an organization’s premises and assets by ensuring that only authorized personnel have access to keys. It also tracks and […]
What is the Key Management System

More and more business security practices are going digital. Every year, it seems like something you took for granted as a physical process is automated or made electronic. Will physical keys be next? We don’t think so. On the contrary, there are many reasons to expect physical keys to be a mainstay of corporate security […]
4 Software Roles with Different Access Layers
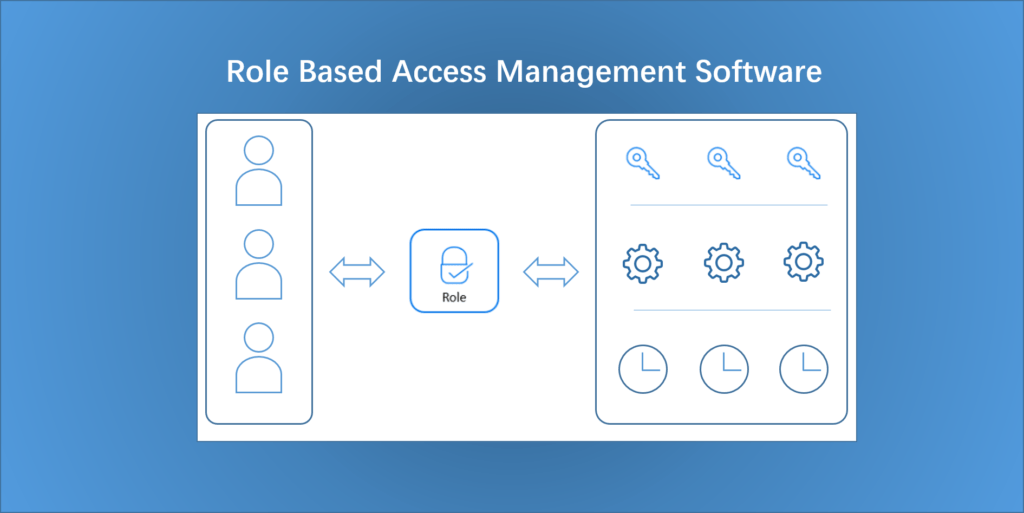
With the implementation of more and more key control systems and the continuous in-depth exploration of market demand, we gradually introduce forward-looking and more market-valuable functions into the management software to ensure that LANDWELL remains at the forefront of the key management field. Today we are pleased to introduce you to this important characteristic of […]
How to send an SMTP Email using standalone i-keybox systems

Although there is no PC or mobile management software in the stand-alone version of the key system, we still hope that our customers will be satisfied with the services provided. SMTP email function has the opportunity to notify customers of abnormal events that occur in the key system, such as timeout access, timeout closing of […]
Landwell‘s 5 Authentication Methods and Their Combinations

Do you have keys? Is there physical keys taking important roles in your business? Are their storage, their management and their transaction secure? Whether you’re a large company, a small business, or even a homeowner, managing physical keys securely has become a top priority. As technology advances, electronic key cabinets have become a reliable solution […]
Hotel Security: Key Control Helps to Prevent Liability

Hoteliers strive to provide a memorable guest experience. While this means clean rooms, aesthetically pleasing surroundings, great amenities and courteous staff, hoteliers must go much deeper to create and maintain a safe and secure environment. The control of room keys is one of the cornerstones of hotel security, and guests are entitled to it in addition […]
Are Smart Key Cabinets Secure?

Are smart key cabinets secure? For most applications, there are strict processes and policies for the access of physical keys. Only measures that comply with these policies and processes can be considered as the basic premise of security. When the surrounding security environment or threats change, our definition and thinking of security will also be […]