With the implementation of more and more key control systems and the continuous in-depth exploration of market demand, we gradually introduce forward-looking and more market-valuable functions into the management software to ensure that LANDWELL remains at the forefront of the key management field. Today we are pleased to introduce you to this important characteristic of software roles. This feature is designed to prevent unauthorized access and simplify key and asset management for organizations of all sizes, providing a flexible and efficient solution for multiple managers within the organization.
Understanding Department
A vertical tree organization structure is always easy to understand, with higher departments able to gain insight into the dynamics of their sub-departments and maintain constant accountability. A department can be your customer, your organization, your group or even a specific employee.
In LANDWELL Key management systems, a “department” is created by the administrator of the parent department and represents a unique entity that contains users, key cabinets and keys, permission groups, reports, and virtually all other administrative resources. The system requires that users can only access equipment that belongs to the same department as they do.
Software Roles
Prior to implementing a key management system, the organization should define permissions for each role to the extent possible. This includes, but is not limited to, defining permissions in the following:
- Access to specific keys
- Registering system resources
- Key authorization management
- Querying key reports
- Switching network modes
1. Common User
The common users are those who use keys, either by applying for them or by being authorized by an administrator to gain access to them, and then log in to the system with their face, fingerprints, passcards, passwords, or a combination thereof, to access specific keys.
2. Administrator
Administrators are created by the department’s system administrator, take on almost all administrative responsibilities other than creating an administrator, and are allowed access to any of the keys.
3. System Administrator
The system administrator is created by the system administrator of the parent department, is unique within the department, assumes all administrative responsibilities, and can access any key.
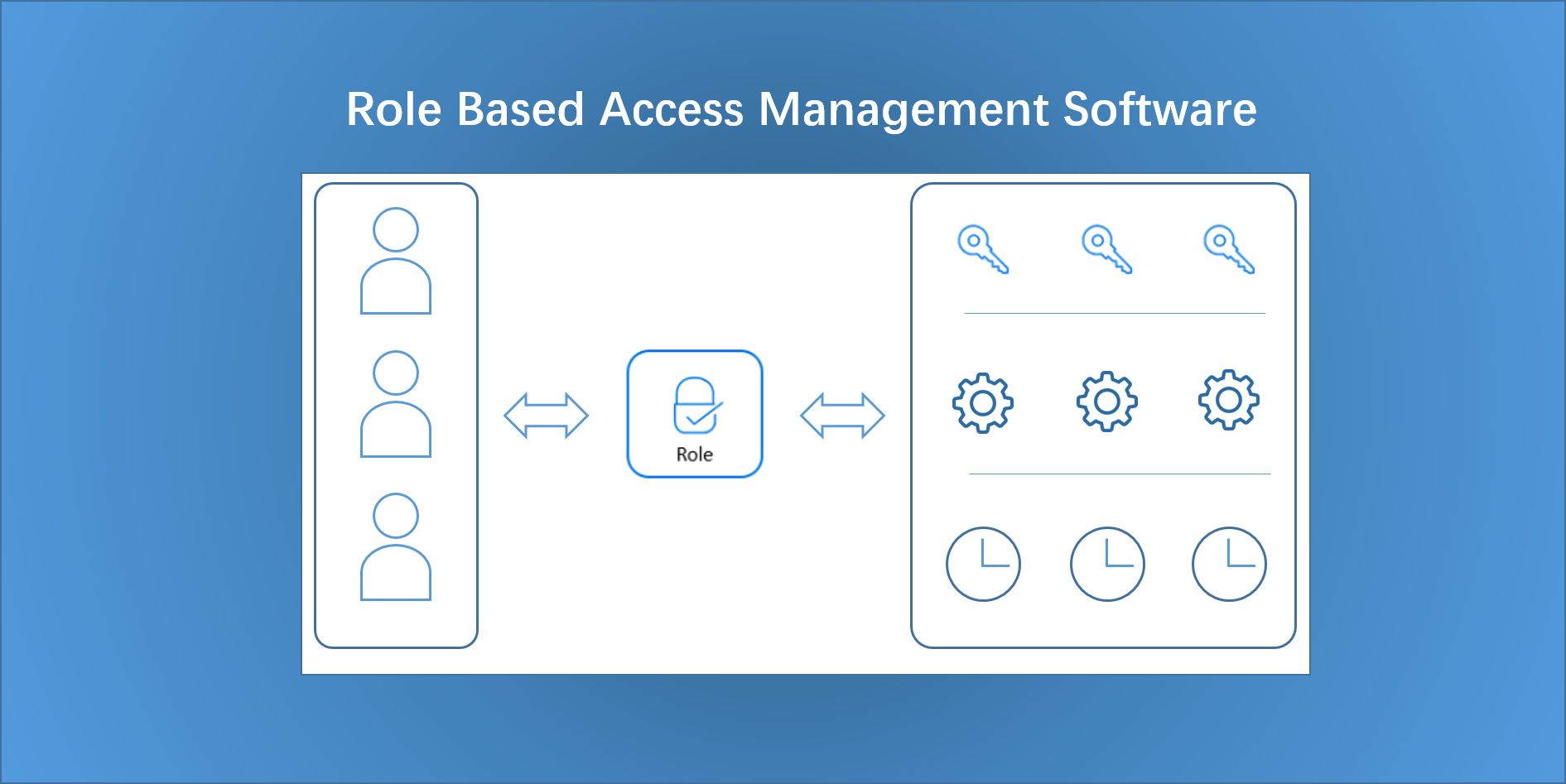
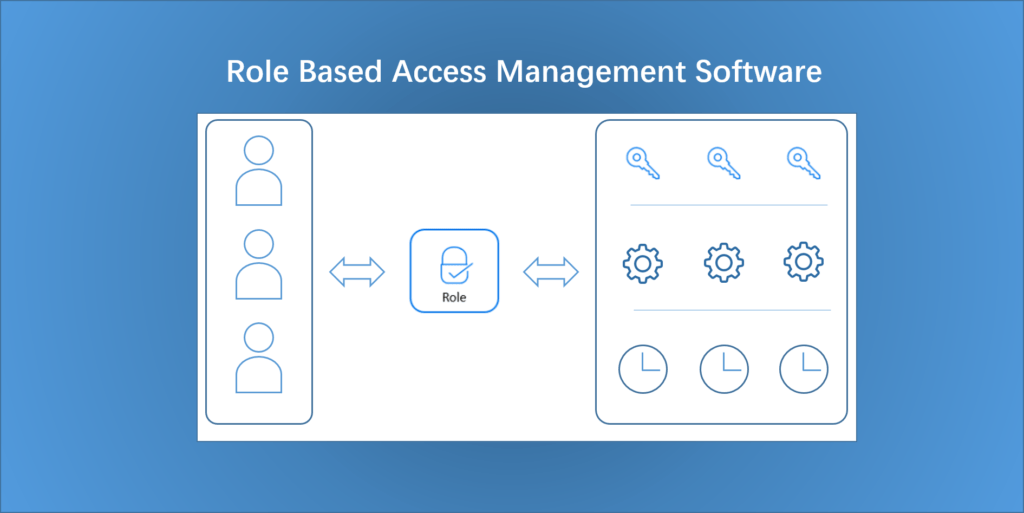
4. Permission Group – Custom Software Role
The system allows for the addition of a customized Permission Group role where members of the group will have the same key access, the same menu access and the same shift schedule.
1) Administrator logs into the system
2) Go to Permission Group Settings and select Add
3) Enter the name of the role
4) Select the menus, keys and schedules they have access to
5) Just save it
How to set a user as a customized role
1)User settings
2) Add or edit a user
3) Role type, select your preset permission group
4)Save it