Introduction
Having excellent control of your keys is essential if you work in a large organization. When there is excellent control over the keys of your industry, you can see the invisibility of key management processes.
You will know who is using your keys at what place and time. It helps you to save your assets with automation, efficiency, and cost savings.
With the help of a key control system, you can avoid risking your fleets, assets, people, and other sensitive information. Security risks are increasing these days, and so is the need for high-quality electronic key control systems. Efficient workforce management demands the use of an efficient control system for keys.
Wondering what makes electronic key management systems important? Lack of proper control over your keys can put your organization’s assets at more significant risk. You can face a lot of losses, such as operational or financial losses.

To ensure that you provide a safe and secure workplace for your employees, it is essential to have an EKMS. EKMS works by using key control software.
Before implementing the electronic key management tool into your organization, you need thorough knowledge. You should know where to implement it and how to get the one that perfectly matches your requirements.
So are you ready to increase the security of your organization and take control over everything? Let’s explore it.

What Is an Electronic Key Management System?
An electronic key management system helps you gain control over your keys for better management of assets. These efficient systems are developed to control, store, and record your keys’ distribution, return, and removal. Only authorized users can access keys managed by the electronic key management system.
You can turn on various security levels for your keys. For example:
- User login, where the system can allow users to log in to the system using passwords, employee cards, fingerprints, face recognition, or a combination thereof.
- Multi-authentication, i.e. two-person rule, for a specific key, the system can require two or three people to authenticate their identity at the same time before they can access it.
- Image capture, the system supports activating the image capture function when the key is removed, so you can easily save the evidence.
- Alerting options, the system will automatically alert emails on abnormal events, including but not limited to the following:
- Key timeout for return
- Overtime for unlocking the door
- Illegal door opening
The above illegal operations will be recorded and displayed in the report. The asset management systems will send you a security report about what happened to the system. The interesting part to note is the use of management software in EKMS.

What Are the Advantages Of EKMS?
You can get multiple benefits through an EKMS. Some significant benefits are given below:
You can have accountability through an EKMS as only authorized personnel can access it. You can create audit trails traces, and report each user’s activity and the key positions. You can also view and print reports.
You gain increased security over your business operations through the help of electronic key management systems. You can create customizable levels of access through an EKMS for tighter control over your assets. You will get an email notification in case of unauthorized access.
You can focus on maximum productivity for your business since you don’t need to worry that your keys will be lost. At the same time, it is easy to operate and use. Foreign nationals, vice premiers, and autonomous regions in china take the most advantage of this system.
What Are Different Operations Available For Key Control Systems?
Taking care of organizational security & to secure keys can be a challenging and daunting task. However, understanding the components of key control systems can make this task easier for you.
By understanding these components, you will know about the availability of different operations in key control systems.
Authentication Technology Of Key control systems
Some key cabinet systems can be accessed through the touch screen like the one in cell phones. This way, you will be suggested the best authentication option for your security. For example, fingerprints, facial scanners, swipe cards, and pin codes.

RFID Tags
The Key Tag is the heart of the key management system. It is a passive RFID tag that contains a small RFID chip that allows the key cabinet to identify the attached key. Since the RFID-based smart key tag technology, the system can manage almost any physical key and has a wide range of applications.

Key Cabinets
You can get key cabinets in various shapes and sizes. They aim to maximize the security of your resources. There is a lock behind a back panel in the advanced key cabinets. You can lock these cabinets into a certain place, and only authorized people or customers can access them.
Some key control systems also come with end cryptographic units.

Smart Terminals

The embedded Android user terminal is the field-level control center of the electronic key cabinet. Big, and bright 7-inch touchscreen makes it friendly and easier to use.
It integrates with smart card readers and biometric fingerprint readers, allowing the vast majority of users to use existing access cards, PINs and fingerprints to gain access to the system.
Management Software For Your Keys
Key management system software helps to monitor and control the whole EKMS. It refers to analyzing reports, managing alarms, and granting personal access.
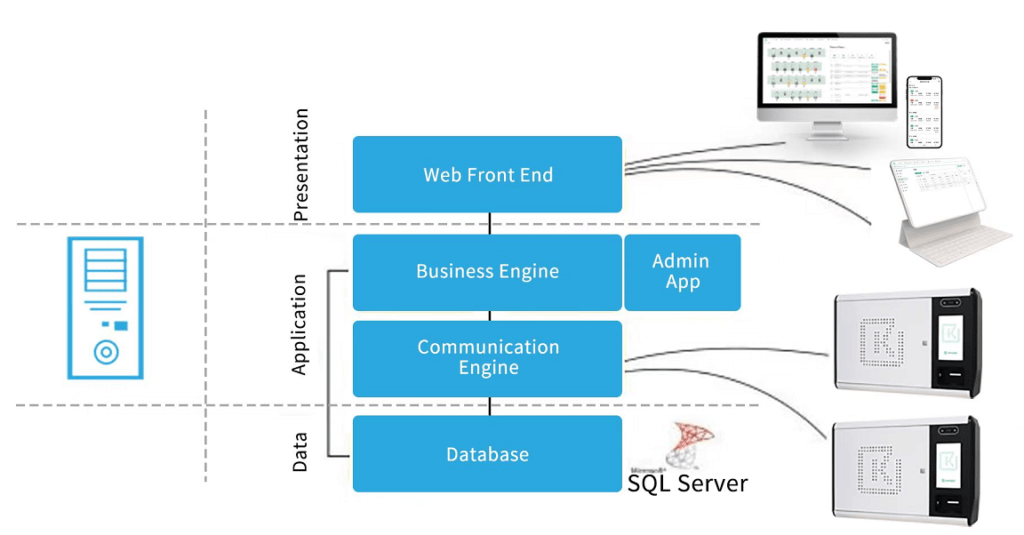
How To Know Needs For Electronic Key Management Systems?
You must determine the seeds for the key generation system if you want to implement one in your company. You can build out your key control needs by following the steps given below:
Evaluation Of Weak Security Spots
When analyzing the needs for EKMS, you have to start by evaluating weak security spots and key control processes. There are chances that you will start risking the errors caused by humans with manual systems.
Some critical points may be sensitive and require higher safety and security. You have to search for that vulnerable point in your system.
Building A Keying Chart
A keying chart is a visual map showing who can access which asset, locker, door, and spaces. It helps you address all those key points or critical places that require higher security.
Determination Of Access Control Needs
Once you have figured out the potential hazards of your organization and made a keying map, you should think of resources that can plug a hole in safety and security. Then, you need to start searching for how you can get the required resources for your organization.

How to Implement Key Control Policies?
When planning to implement policies of the key control systems in your organization, you need a perfect partner. You need someone to help you achieve security goals and other services at affordable or competitive pricing. You need to check the websites of multiple vendors.

How To Choose The Right Brand For Your Key control?
You need to follow some basic steps one by one:
Taking Current State Inventory
You must take inventory of all the assets and needs you want to secure. After getting an estimate, You can compare the manufacturing facilities. You need to ask if the particular vendor or company can help you manage this number of assets or keys.

Determine Your Reporting, Security, and Access Needs
Make sure that your chosen supplier can fulfill your security needs. For example, do you need to secure your assets using biometric readers, PINs, or facial expressions? You need to ask the following questions:
- Do the keys have real-time reporting and tracking?
- Do they provide alerts if keys are not returned?
- Do they allow you to remove or restrict access remotely?

Future Preparation
Just thinking about your needs is not the only thing you should do. You have to invest some time in choosing the right partners. It will save you time and money in the future. You need to ask the following questions in this case:
- Will they allow me to expand?
- Is it necessary to replace key fobs? If yes, then how much will the cost be?
- Is it necessary to keep the key fobs clean?
- Are there maintenance procedures required for the system? How much will it cost?
- Does the hardware quality meet the requirements?
- How long is the delivery time of the product?
- Does the supply capacity meet the demand?
- Is there a warehouse and inventory?
- Does it support customized services?
- Is after-sales service guaranteed?
- Can you provide complete and reasonable solutions?
- Is there any test report?
- What is the minimum order quantity?

Software and Reporting
Electronic key management systems have an important part as the software that manages them. To get guidance on your reporting and software choice, you must ask the following questions:
- How many people are allowed by the software?
- How many user profiles and administrative are allowed?
- Is it possible to create custom alerts and reports?
- Is it possible to turn on alerts on late keys?
- Is it possible to export reports? If yes, how can the system give reports according to my needs?

Checking Integration
It is important that your electronic key management system should get along with other applications. Otherwise, you will end up frustrated. You must ask some questions related to integration given below:
- Can you integrate the system with existing physical security systems?
- Can it make a connection with other applications?
- Is it possible to connect cabinets across different sites for a centralized system?

Tying Up The Odds and Ends
In the end, you need to ask these supplementary questions from your partner:
- Can I reserve the keys?
- Can I restrict the keys according to time?
- Can I perform fleet management through this system

Conclusion
Setting up an electronic key management system for your organization is the best decision that you can make. However, choosing the right vendor also affects this decision a lot. To ensure you get the right system for your key control, you must implement the whole method explained above.
Having a safe and secure administration of your place can attract more people.
Why Choose LANDWELL?
✅LANDWEL is a multinational enterprise with a high reputation in China.
✅The company focuses on innovative and market-oriented solutions for its 100,000+ users.
✅There is a huge role of LANDWELL in the automation industry of China.
✅With more than 20 years of experience, LANDWELL can be your best vendor for electronic key management systems.
✅Look no further. Contact Us now. We are happy to support you with your security needs in any country at a competitive price.




